nfs持久化存储
参考资料:https://blog.51cto.com/14306186/2522546
阿里提供的一个开源镜像“nfs-client-provisioner”,这个东西是通过k8s内置的NFS驱动挂载远端的NFS服务器到本地目录,然后自身作为storage(存储)。
注意:以下的命令空间都需要单独设置
Storage Class自动创建PV
搭建nfs服务
作者把nas作为nfs服务器,没有的可以master机器做服务器
[root@master ~]# yum -y install nfs-utils
[root@master ~]# systemctl start rpcbind
[root@master ~]# systemctl enable rpcbind
[root@master lv]# mkdir -p /nfsdata
[root@master ~]# vim /etc/exports
/nfsdata *(rw,sync,no_root_squash)
[root@master ~]# systemctl start nfs-server
[root@master ~]# systemctl enable nfs-server
[root@master ~]# showmount -e
Export list for master:
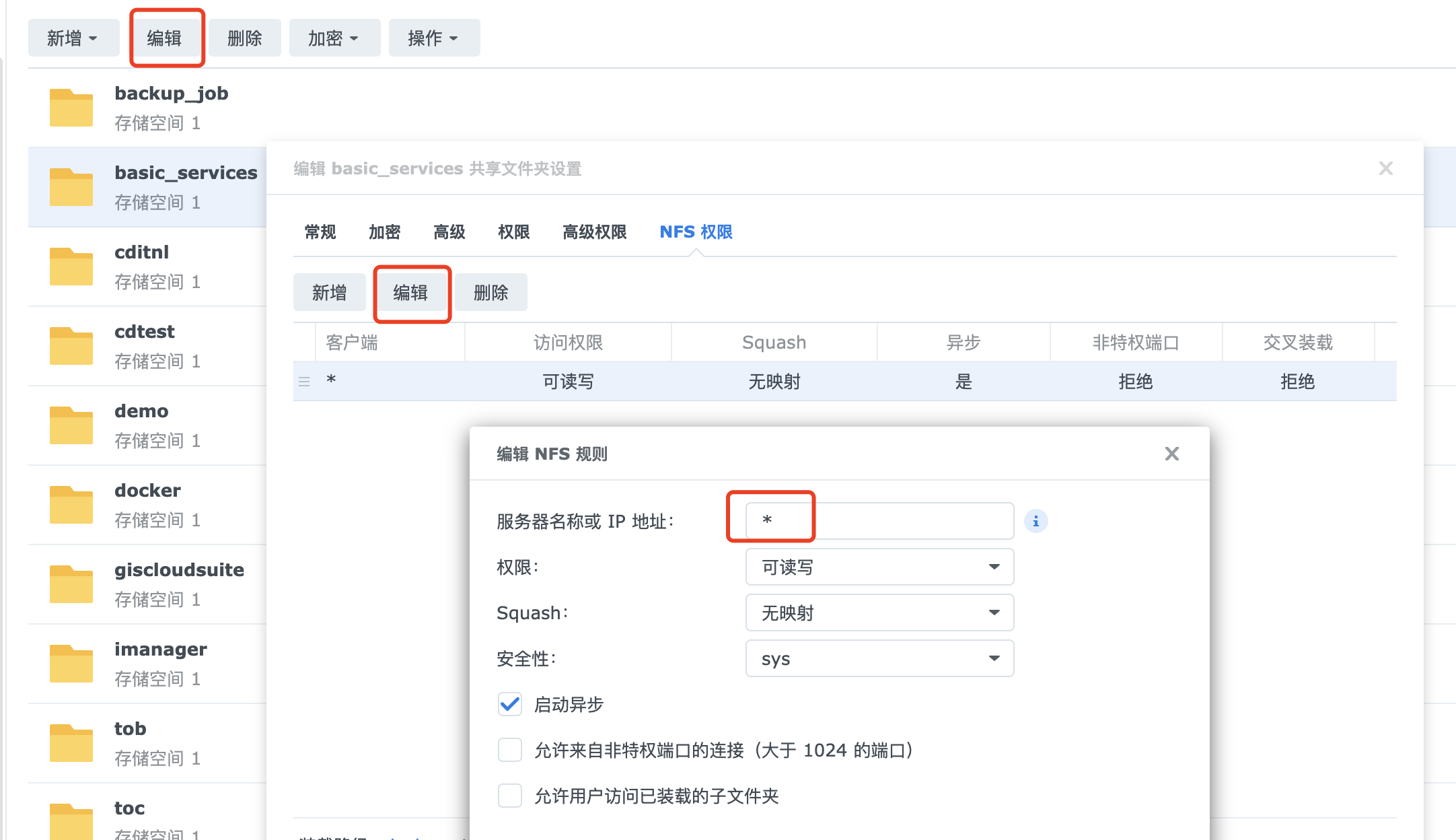
/nfsdata *作者用的群辉nas,系统自带nfs服务器,需要开启nfs服务,然后给创建的共享文件夹设置nfs权限
创建rbac授权
这种自动创建pv的方式涉及到了rbac授权。
- 创建一个用于认证的服务账号
- 创建群集规则
- 将服务认证用户与群集规则进行绑定
apiVersion: v1
kind: ServiceAccount
metadata:
namespace: devops
name: nfs-provisioner-devops
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
namespace: international
name: nfs-provisioner-runner-international
rules:
- apiGroups: [""]
resources: ["persistentvolumes"]
verbs: ["get", "list", "watch", "create", "delete"]
- apiGroups: [""]
resources: ["persistentvolumeclaims"]
verbs: ["get", "list", "watch", "update"]
- apiGroups: ["storage.k8s.io"]
resources: ["storageclasses"]
verbs: ["get", "list", "watch"]
- apiGroups: [""]
resources: ["events"]
verbs: ["watch", "create", "update", "patch"]
- apiGroups: [""]
resources: ["services", "endpoints"]
verbs: ["get","create","list", "watch","update"]
- apiGroups: ["extensions"]
resources: ["podsecuritypolicies"]
resourceNames: ["nfs-provisioner"]
verbs: ["use"]
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: run-nfs-provisioner-international
subjects:
- kind: ServiceAccount
name: nfs-provisioner-international
namespace: international
roleRef:
kind: ClusterRole
name: nfs-provisioner-runner-international
apiGroup: rbac.authorization.k8s.io创建nfs-client-provisioner容器
其实它是一个NFS客户端。但它通过K8S的内置的NFS驱动挂载远端的NFS服务器到(容器内)本地目录;然后将自身作为storage provider,关联storage class。
关于指定pod调度到某个节点可以使用nodeSelector,我这里是使用tpye,需要先给节点打上标签
kubectl label nodes master type=master
kubectl label nodes node1 type=node1
kubectl get nodes --show-labels 查看
注意:不打标签,则状态会pendingapiVersion: apps/v1
kind: Deployment
metadata:
name: nfs-client-provisioner
namespace: devops
spec:
selector:
matchLabels:
app: nfs-client-provisioner
replicas: 1
strategy:
type: Recreate
template:
metadata:
labels:
app: nfs-client-provisioner
spec:
nodeSelector:
type: k8s
serviceAccount: nfs-provisioner-devops
containers:
- name: nfs-client-provisioner
image: registry.cn-chengdu.aliyuncs.com/liuchenyun/nfs-subdir-external-provisioner:v4.0.2
volumeMounts:
- name: nfs-client-root
mountPath: /persistentvolumes
env:
- name: PROVISIONER_NAME
value: basic-services
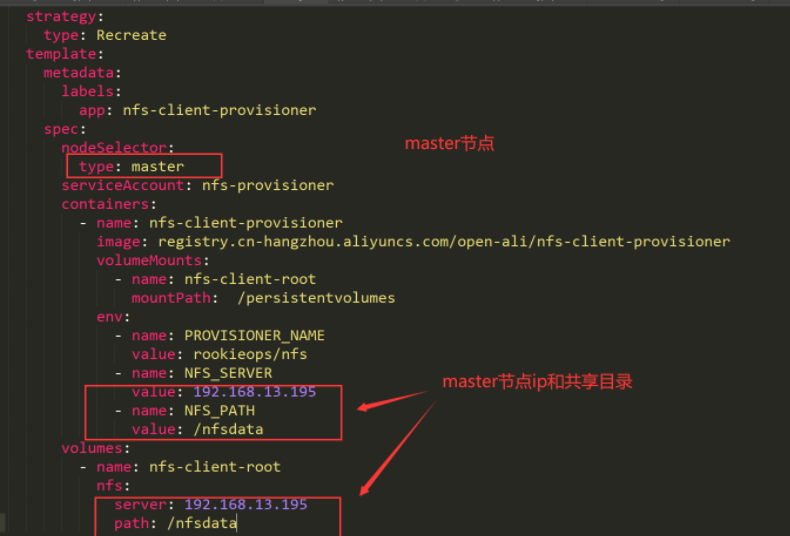
- name: NFS_SERVER
value: 192.168.31.156
- name: NFS_PATH
value: /volume1/basic_services
volumes:
- name: nfs-client-root
nfs:
server: 192.168.31.156
path: /volume1/basic_services
imagePullSecrets:
- name: dockercfg-liuchenyunnodeSelector:
type: k8s // 自己打的标签的机器
env:
- name: PROVISIONER_NAME
value: basic-services // 与下面的sc配置的provisioner相同
- name: NFS_SERVER
value: 192.168.31.156 // nfs服务器ip
- name: NFS_PATH
value: /volume1/basic_services // nfs服务器共享的目录
serviceAccount: nfs-provisioner-devops // 跟授权账号名保持一致创建SC(StorageClass)
kind: StorageClass
apiVersion: storage.k8s.io/v1
metadata:
name: basic-services
namespace: devops
provisioner: basic-services
reclaimPolicy: Retainprovisioner: basic-services // 与Deployment中环境变量PROVISIONER_NAME相同
reclaimPolicy: Retain // 指定回收策略为手动nas上授权nfs